Blockchain Explained - What is blockchain technology?
What is blockchain?
Blockchain quite literally is a set of blocks containing data, that have been chained together, one on top of another. The first block in the chain is aptly referred to as the "genesis block". Blockchain is also considered to be the asset exchange protocol that is the underlying architecture/protocol of Bitcoin. However, blockchain transcends Bitcoin.
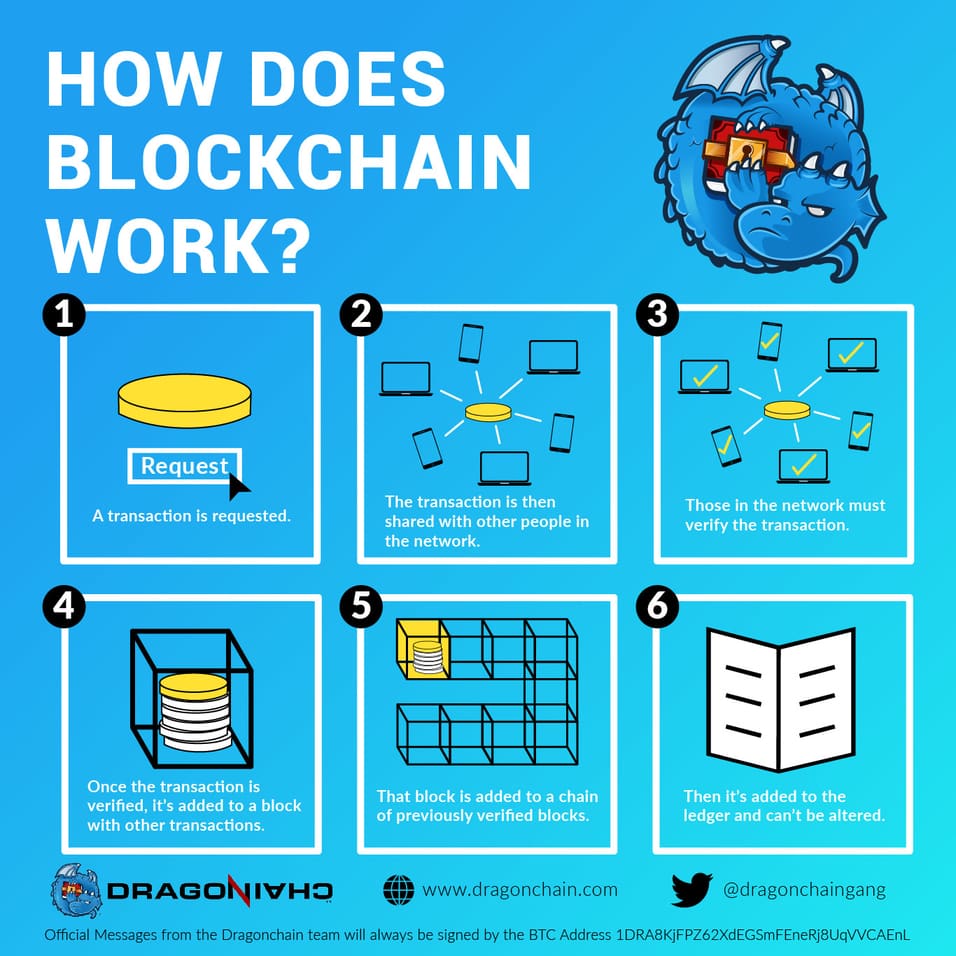
How does blockchain work?
Blockchain technology creates a shared, single source of the truth that can be easily verified via math. Some of the greatest benefits of value added by blockchain are:
- Blockchain allows us to store digital value, such as money or data, mathematically, with no middleman.
- The ability to define the state of any digitized object or transaction of that object, at any particular point in time.
- Greater transparency, which benefits traceability, efficiency, speed. And also eliminates friction between parties.
- More secure transactions, and redefined data access management.
- Arguably cost reduction for governments, organizations and enterprises. Although research & development with initial investments for proof of concepts are required.
Early 1990's
Newspaper comparison helped humans understand the concept of the internet. Today, we see that the mainstream has adopted internet technology, and, that technology is much more than a digital newspaper.
2010's & 2020's
Today, we see many educators using digital payments to help describe blockchain technology. This is most likely an underestimate of a very disruptive technology.
We are now starting to learn how to build structures on top of that network. Dragonchain provides easy blockchain onboarding, development, support, training, and mentoring toolset for any idea, company, technology, or individual.
Already know what blockchain is? Learn the differences between types of chains, such as private, public and hybrid blockchains.
Peer-to-peer cash
Blockchain caught popularity when the famous Bitcoin whitepaper, written by Satoshi Nakamoto, was released in October 2008. It describes a purely peer-to-peer system allowing money to be sent directly from one party to another without going through a central authority such as a financial institution.
The concern revolves around sending electronic cash from one person to another. This is the current system with banks. Banks are updating and maintaining at least two databases, each of which need to be constantly updated. (Double-entry accounting)
Suppose I deposit $1,000 in my bank account. They update the database and it points to a record that I have $1,000. Let's say I want to send $10 to Ann Marie. Take $10 from my account and record $10 in Ann Marie’s account. Those separate databases must synchronize in order for the $10 to leave my account and enter Ann Marie's.
There is an inherent weakness in the trust model, which is the need for a middleman. I can’t send it to you directly without this bank in the middle. With the Bitcoin block chain, I can.
If you read this on the Dragonchain Academy instead, we can track that you read the entire content, you can take a knowledge quiz, we will reward you in Dragons and give you a free certification, all on blockchain!
Double Spend Problem
Unlike when we take a picture with our phone and send it to a friend, I still have a copy of that picture. Obviously, with money, you can’t do that. A person who spends money can no longer have possession of that money. This creates what we call the "double spend problem." The Bitcoin network, for the first time, solves that double spend problem with the middleman. It does this by using math and computational power. That is the innovation.
Blockchain Definition
A blockchain is a time-stamped series of immutable data that is managed by a cluster of distributed networks or computers. Each of these blocks of data are secured and bound to each other using cryptographic principles creating a "chain" of blocks. Blockchain is distributed, immutable, and cryptographic data that provides anonymity and transparency.
A blockchain uses two important data structures:
- Pointers. Variables in programming which store the address of another variable. Usually normal variables in any programming language stores data. Eg. int a = 10, means that there is a variable “a” which stores integer values. In this case, it is storing an integer value which is 10. This is a normal variable. Pointers, instead of storing values will store addresses of other variables. This is why they are called pointers, because they are literally pointing toward the location of other variables.
- Linked List. A sequence of blocks, each containing data which is linked to the next block via a pointer. The pointer variable, in this case, contains the address of the next node within it, thereby the connection is made. The last node, as you can see, has a null pointer which means that the pointer has no value. One important thing to note here, the pointer inside each block contains the address of the next block. That is how the pointing is achieved.
What is a transaction?
A transaction is the basis which all events or data transfers are recorded within the blockchain platform. The system should define a flexible and extensible standardized transaction structure.
Implementation options:
- JSON with standardized structure
- JWT (JSON Web Token)
- Other encoded structure (with supporting libraries in multiple languages)
JSON (JavaScript Object Notation) is a lightweight data-interchange format.
- Easy for humans to read and write & easy for machines to parse and generate.
- Based on and built into the JavaScript Programming language.
JSON is built on two structures:
- A collection of name/value pairs. In various languages, this is realized as an object, record, struct, dictionary, hash table, keyed list, or associative array.
- An ordered list of values. In most languages, this is realized as an array, vector, list, or sequence.
These are universal data structures. Virtually all modern programming languages support them in one form or another. It makes sense that a data format that is interchangeable with programming languages also be based on these structures.
JSON Web Token (JWT)
An open standard (RFC 7519) that defines a compact and self-contained way for securely transmitting information between parties as a JSON object. This information can be verified and trusted because it is digitally signed. JWTs can be signed using a secret (with the HMAC algorithm) or a public/private key pair using RSA.
Key Concepts
- Compact: Because of their smaller size, JWTs can be sent through a URL, POST parameter, or inside an HTTP header. Additionally, the smaller size means transmission is fast.
- Self-Contained: The payload contains all the required information about the user, avoiding the need to query the database more than once.
Supporting libraries in multiple languages.
- Developers may also code smart contracts on Dragonchain in Java, Python, Node, C#, or any other language.
Transactional Packets of Data
- Header
- Payload
- Signature
Header
Contains system or network defined standard metadata fields for the transaction.
Example fields:
- Transaction ID
- Transaction type
- Transaction class
- Create timestamp
- Transaction timestamp
- Origin ID
- Business organization and/or organization taxonomy
- Actor
- Entity
Payload
Arbitrary structure and content that is defined at the business level and implemented or controlled within the level 1 approval code.
Some level of structure within the payload (e.g. fields and structures) may be implemented as network wide templates to be utilized and noted based upon the optional transaction class header field. This will allow nodes to implement some needed behavior defined at the enterprise or network level, along with simplification of capabilities such as currency.
Classes
Transaction class examples:
- Default (custom Level 1 business payload structure)
- Currency provisioning
- Network communications
- Marketplace transaction
- Information interoperability (foreign blockchain currency or information payload)
Signature
A portion of the transaction holding a cryptographic signature to allow parties to prove the source and/or that the contents of the transaction are unaltered since the signing (i.e. tamper evident). The signature within the transaction should not be required from the transaction source (e.g. client or 3rd party system) as some clients may not be cryptographically enabled or aware of the blockchain platform. Alternatively, a client system, for example, may invoke a process of multi-party signing prior to transaction submission. Either way, the node’s transaction service component should cryptographically sign any inbound transaction that it accepts for processing (with its configured key pair).
Perceived Requirements:
- The structure should allow for multi-party and nested signings
- The signature should hash all fields within the signature structure itself minus hash and signature to make the signature itself tamper evident
- The structure should see re-use in the verification record (block verification) signing process
Fields:
- Signatory
- Hash
- Stripped hash (for transaction signatures only - a hash of the full transaction with the payload stripped - to allow level 2+ nodes to validate a transaction even when the payload is not available)
- Public key
- Signing timestamp
- Signature
- Child signature (optional)
Block Definition
Block definition may see multiple implementations, although there are more or less common elements involved such as:
- Block ID
- Timestamp
- Transactions
- Hash of prior block
- Proof (e.g. PoW, PoS) artifact
- Signature
- Block period
- Verification attributes
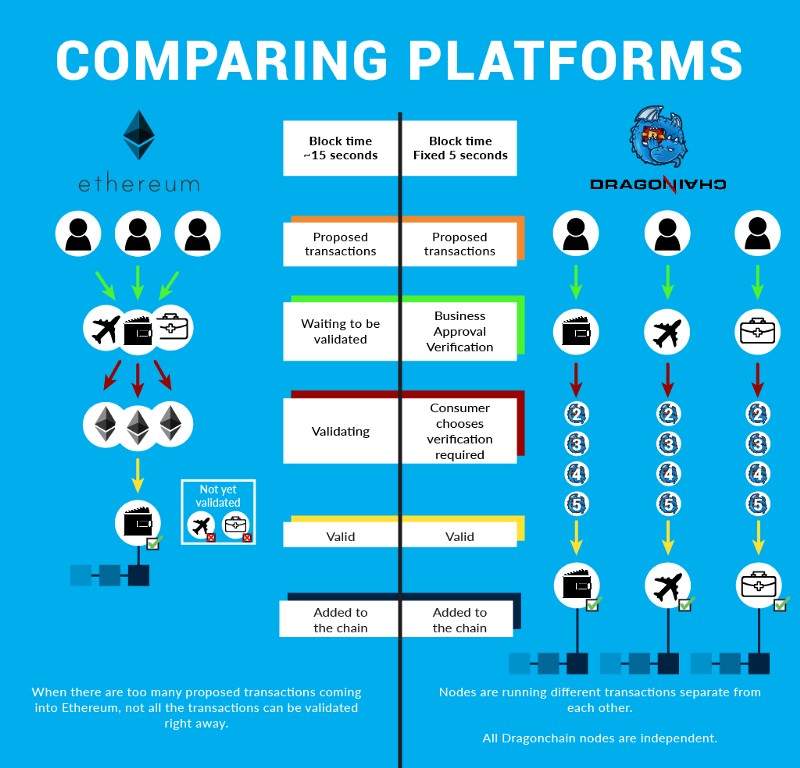
An interesting part of block definition design that is the question of when the block is formed. In Bitcoin or other proof of work systems, a block is formed when the proof of work algorithm is solved for the current network difficulty. This may happen after 30 seconds or 30 minutes. It is variable and random, but the network seeks to tune the difficulty in order to tune the average block time to 10 minutes in Bitcoin.
We refer to this design methodology as Heuristic Design (hd). (hd) makes the mining problem harder should it fall below the 10-minutes on average, to get back up or above the 10-minute average.
In trust-based systems, there would be no absolute need to maintain a variable time based block. In many real world systems, it is in fact seen as a detriment to its use that Bitcoin cannot offer a fixed or faster average block time. In this architecture, we may desire a more appropriate block time, such as a fixed time in seconds (e.g. 5 seconds). The definition of such fast and fixed block times leads to a question of consensus, that is, with context based verification and the concept of a “blockchain of blockchains”, the system comes to gradual consensus with risk controlled by individual business users.
Centralized, Decentralized, and Distributed Hybrid Blockchains
Centralized systems require permission to participate and have full control over data in the network. This makes it hard to share data across networks.
Decentralized systems are controlled by no single authority. All network transactions are available publicly. This public accessibility can cause concerns for security of the data.
The Dragonchain hybrid public-private blockchain solution allows the data to be seamlessly connected between the two system types. This allows users to selectively share portions of the data or business logic with a public blockchain, without risking the security of the private business data.
Immutable Ledgers of Chained Data
Immutable simply means unchanging over time or unable to be changed. By design, a block chain is immutable once recorded, and data on the blockchain cannot be changed retroactively without the alteration of all of the previously written blocks.
Cryptographic Data
Data that has been stored using a cryptographic method to hash the source, using some type of encryption algorithm.
Anonymous and Anonymity
Anonymous and anonymity are derived from the Greek words ἀνωνυμία, or anonymia, meaning "without a name" or "namelessness". When discussing data, is the ability to have shielded/blinded transactions, or, a portion of that transaction or data is shielded/blinded so that it cannot be tracked or traced to the source.
Transparency
Transparency means operating in such a way that it is easy for others to see what actions are performed. It is simply defined as, "The perceived quality of intentionally shared information from a sender."
- Openness
- Communication
- Accountability
What is the difference between centralized and decentralized?
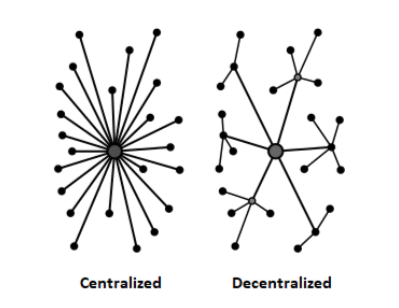
In decentralized systems, complex behavior occurs at lower levels, operating on local information, not the instructions of any commanding influence. This form of control is known as distributed control; each component of the system is equally responsible. The lower-level components are implicitly aware of these appropriate responses through mechanisms that are based on the component's interaction with the environment.
What is Distributed?
Distributed systems are located on different networked computers, which communicate and coordinate their actions through a series of messages. The components work in tandem to achieve a common goal.
What is Open source?
Open source is made freely available and may be redistributed and modified.
What is cryptography?
The art of writing or solving codes.
What is modern cryptography?
Modern cryptography is heavily based on mathematical theory and computer science practice. Cryptographic algorithms are designed around computational hardness assumptions which make these algorithms hard to break in practice by any adversary. It is theoretically possible to break such a system, but not practical to do so.
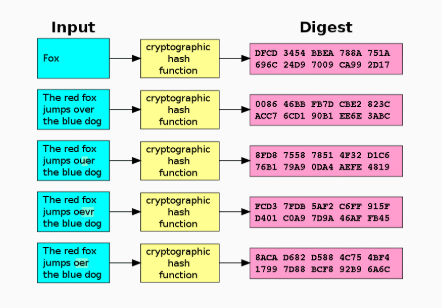
What is a Hash function?
A hash function is any function used to map data of arbitrary size into data of fixed size. The values returned by a hash function are referred to as hash values, hash codes, digests, or simply hashes.
What is a crytographic Data Hash?
With cryptographic data hashes, mathematical algorithms map data of arbitrary size to a bit string of fixed size (a hash) as part of a one-way function.
A cryptographic hash function at work. A small change in the input (in the word "over") drastically changes the output (digest). This is the "avalanche effect".
What is SHA-256?
Secure Hash Algorithm 256(SHA-256) is a common cryptographic hash (sometimes called 'digest') that serves as a kind of 'signature' for a text or a data file. It is currently the method used by bitcoin. SHA-256 generates an almost-unique256-bit(32-byte) signature for a text.
What is consensus?
In cryptography, consensus is needed to record and verify transactions through mathematical problem-solving for storage in a digital ledger.
Consensus
A consensus algorithm is a process in computer science used to achieve agreement on a single data value among distributed processes or systems. Consensus algorithms are designed to achieve reliability in a network involving multiple unreliable nodes.
Trust (Default)
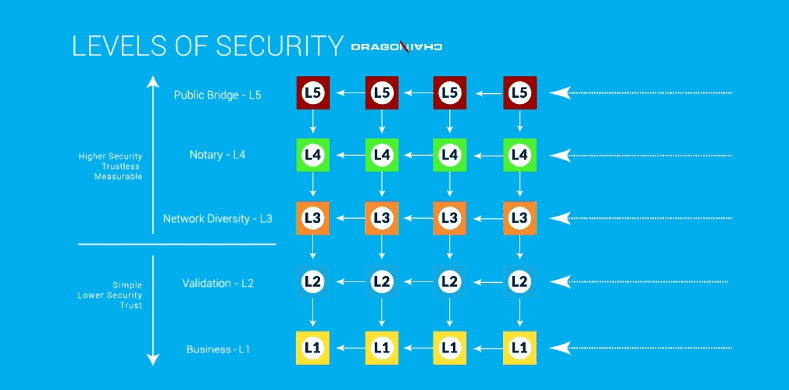
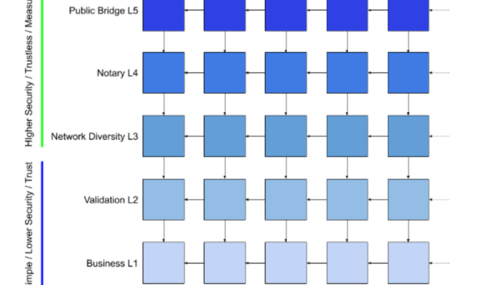
Every organization depends on trust, in one form or another, among users of the system. In general, different forms of trust exist to address different types of problems and mitigate risk in certain conditions. The form of trust to apply in a given circumstance is generally dictated by corporate policy. Dragonchain will provide a spectrum of trust for the consumer of blockchain data, where risk is accepted based upon a combination of real world contracts, reputation of nodes, and trustless system assertions. That is, one may trust one’s own data as valid, but require varying levels of consensus verification before accepting a partner or foreign node for use. The system will provide a human readable report as well as API access to this capability.
Proof of Work (PoW)
Proof of work is just that, Proof that work has been done. It can be traced back as early as the Giza plateau. The Pyramids clearly prove that work was performed so many years ago. This proof has lasted thousands of years. With cryptography, we create Proof of work (PoW) in much of a lottery type method where the lottery participants are the nodes/miners. Once the block has been mined, the other miner will verify and be the administrative body. Once a block has been mined, it is extremely easy for the other miners to verify the newly mined block.
Miners are doing the mathematical requirement to define an expensive computer calculation, also called mining. The expense comes from the power used to perform the calculation. In Bitcoin, each block is mined every 10 minutes. With Dragonchain, each block can be mined as quickly as 2 seconds depending on the the proof level required. Mining must be performed in order to create a new group of trustless transactions or the block on a distributed ledger that we refer to as "blockchain".
Key concepts of proof of work:
- Miners compete to see who can create each block first.
- First miner to solve the problem is rewarded, the other miners check the work of the successfully mined block and come to consensus that it is accurate.
- Miners compete to be first. If they are not the creator of the new block the effort is wasted and so is the power used.
Proof of Stake (PoS)
Proof of stake isn't so much about mining, but more about verifying and creating. It requires miners to "stake" to create blocks. The miner is limited to mining a percentage of transactions that is reflective of his or her stake.
Stake could be random, some amount of wealth staked or age of the miner among others. Rewards are not given to miners. Miners are paid the transaction fee. Miners are able to mine transaction of higher value if they have a higher stake.
Unlike Proof of work, proof of stake does not waste computing power as the miners are not in contention to mine the same blocks.
Key concepts of proof of stake:
- A miner has some "stake" in the game. This stake could be age, wealth, or random.
- Incentive is transaction fee not reward.
- This consensus method can be several thousand times more cost effective than proof of work.
Other consensus Algorithms
These are all possible methods to be considered or used:
- Proof of activity
- Proof of elapsed time
- Proof of burn
- Proof of human
- Proof of knowledge
What are Encryption Algorithm Types?
Encryption algorithms are the mathematical computations on data, used to produce the hash results. Encryption Algorithms come in 2 basic types:
- symmetric
- asymmetric.
Symmetric Encryption
Algorithms used in cryptography that use the same cryptographic keys to encrypt plaintext and decrypt ciphertext.
The keys may be identical or there may be a simple transformation to go between the two keys.
The keys, in practice, represent a shared secret between two or more parties that can be used to maintain a private information link. This requirement, that both parties have access to the secret key, is one of the main drawbacks of symmetric key encryption.
Asymmetric Encryption/Public Key Cryptography
Public key cryptography is a cryptographic system that uses pairs of keys. It incorporates public keys, which may be disseminated widely, and private keys, which are known only to the owner.
In a public key encryption system, any person can encrypt a message using the receiver's public key. That encrypted message can only be decrypted with the receiver's private key.
Public key algorithms are fundamental to cryptosystems, applications and protocols. They underpin various internet standards, such as Transport Layer Security (TLS), S/MIME, PGP, and GPG.
Secure signatures
Private key is used to sign a packet of data. Public key is used to verify private key signature. This is done with the goal of creating authenticity.
Interchain
Interchain™ is a combination of smart contracts that can watch a blockchain of the user’s choice for incoming transactions and fire smart contracts on Dragonchain or another public blockchain. It allows users to connect one blockchain platform to another. This simple process redefines the use of blockchain technology, allowing users to conduct processing across blockchains.
Interchain’s capabilities include:
- Watching the transactions on the chain and/or address of a user’s choice
- Firing smart contracts on Dragonchain or other public blockchains
- Moving tokens or currency on Dragonchain or other chains
- Using a public blockchain for a transparent process of selective parts of the user’s business logic
Developers on your team can write smart contracts in coding languages they’re familiar with, using our SDKs. Building your first prototype on the blockchain no longer takes months to complete. And deploying your first block chain can be done in a matter of minutes. Our Blockchain as a Service is focused on rapid blockchain development without sacrificing any critical features.
Explore blockchain platform features.
Time Fixation Before Blockchain
Previously, we had the ability to present proof that something happened through a photograph. The photographic evidence only proved that something had happened, but it was hard to pinpoint exactly when something happened.
Time Fixation in Present Day
The event occurs between two points in time with a measurable proof allows us to order events. This simple order of events is a process that prevents double spending.
First Time in Human History this is Possible!
What could be possible with software and systems built to open up markets that otherwise would not exist? It does this by combining marketplace capabilities with software.
So, What Exactly is Time?
Triple Entry Accounting (Double-entry + Cryptography)
is an enhancement to the traditional double-entry system in which all accounting entries involving outside parties are cryptographically sealed by a third entry. These include purchases of all types of transactional data including traditional accounting attributes such as inventory, supplies, sales, tax, utility payments, and other expenses. Placed side by side, the bookkeeping entries of both parties to a given transaction are congruent. A seller books a debit to account for cash received, while a buyer books a credit for cash spent in the same transaction, but in separate sets of accounting records.
Blockchain provides a digital signature along with a time stamp and chain of records that keep the sets of books along with a hash of the data in the previous blocks that chains the data together.
These transactions occur in the form of a transfer between wallet addresses in the distributed ledger, creating an interlocking system of enduring accounting records. Since the entries are distributed and cryptographically sealed, falsifying them in a credible way or destroying them to conceal an activity is practically impossible.
The Real Power Behind Blockchain and Cryptocurrency
The software is providing the kernel of value by creating marketplace capabilities on nearly any asset that can be digitized. Nearly anything can be digitized including time. What marketplaces currently exist using time as the exchangeable asset?
The software is self-driven in that Satoshi didn't travel the world to explain the power of Bitcoin software. The software itself negotiated these hurdles with very little human intervention. Any sufficiently modeled software economy should drive adoption and business community goals with incentives. This is exactly what Bitcoin did.
A well-designed marketplace may arguably be faster. Why? If you are using people and their minds and information to find ways to profit, it will happen. We see this with Bitcoin. The Bitcoin algorithm incentivized people to mine and potentially - over time - provided the ability for people to use the technology. The simple currency exchange technology has not been broken and has been proven to work well.
Custom Currencies Can Track Behavior
With custom currencies and enterprise environments, we have the ability to look at all the data and define what we consider a good or bad actor. The enterprise can then incentivize the system to reward good behavior. What types of things could have value as a digital asset and be tracked that traditionally would not? If anything can be a digital asset, then everything is a marketplace that we exchange as digital value.
- Assets can be used to track and incentivize behavior.
- The software can track and trace asset behavior, regardless of how the digital asset has been defined.
- Analytics can be used to help create incentives to encourage certain types of asset movement or behavior.
How to Further Adoption for Real Business
Flexibility
Enterprise businesses require flexibility in the software they use. Many times when looking at blockchain solutions; flexibility tends to be a big problem. This is prevalent when evaluating blockchains that are only public. Public blockchains may store sensitive business data on a public ledger, which is not ideal or an option for most enterprises. Real businesses with real customers require control over their sensitive data.
With a hybrid approach, sensitive and proprietary business data can be kept secure on a privately distributed ledger using smart contracts written in a programming language you understand. This approach is also providing proof of status as an artifact on a public chain.
Resources Needed for a Blockchain Solution
- A wealth of libraries or programming code that is used to develop software programs and applications
- Wrap traditional libraries in smart contracts
- Interchaining with chains for most needed features
- Selective decentralization
- Use of oracles as the golden source for data collection
- Selective exposure
Simplification
Simplification can be achieved by adopting an easy to use and powerful platform that takes advantage of the power, functionality, and capabilities that are driving factors for adoption.
A hybrid approach allows you to bypass many drawbacks of traditional innovation by utilizing tried-and-true technology while adopting the power of the blockchain. This hybrid approach must aim to keep things simple, as simplification has traditionally helped drive adoption.
- Separation of skill sets
- Ability to harness experience of traditional developers
- Best dev-ops practices (20+ years)
- Blockchain-based micro-services
Blockchain technology has been getting a lot of attention for its industry-disrupting capabilities. As a result, many industries are falling over themselves trying to incorporate blockchain.
However, should all companies have a blockchain initiative? How can enterprises put themselves into the right position for success?
What are the things that one must consider before incorporating blockchain technology?
Skill Set Challenge
Leveraging blockchain technology for real business initiatives is expensive and risky in an operational environment.
This can be expected to result in low success rates because the creation of software without blockchain capabilities is already fraught with difficulties. The addition of a relatively new technology such as blockchain with features such as cryptography, proof of work, economics, currency modeling, game theory, and custom programming languages are sure to cause more trouble for a team as the overlap of these skills is particularly rare.
Dragonchain solves this problem by allowing development and integration before the economic model is known. Monetization can be applied after a system is functioning and enough real data is available for analysis
Juniper Research
Researchers asked employees of some big companies (with >20,000 employees) whether they are looking to incorporate the blockchain. 57% said “Yes” while only 9% said “No”.
Blockchain Considerations"If it works, don't fix it"
There are many companies out there who are desperately trying to incorporate blockchain into their business, despite already having perfectly functional systems in place. . The idea that “everything should be decentralized” is wrong. Let’s take the example of Amazon. Amazon is a multi-billion dollar e-commerce giant. The biggest factor behind their growth is their UI/UX. If you order something on Amazon, you will get it within a day. If you don’t like it, Amazon will take it back within a day and refund you. Why would you want to disrupt such a great service by incorporating a new piece of technology that you have no experience with?
More often than not, if you are looking to increase the efficiency of your company, the answer may very well lie in reworking certain legacy-based solutions to take advantage of a characteristic of the technology as a proof of concept. Take small portions of data to the blockchain instead of jumping onto the blockchain wagon and trying to rebuild everything.
There is no doubt that blockchain technology has many brilliant use cases that will provide major benefits. However, this technology requires time to develop and deploy. How can you be best positioned yourself to adopt features as they become available?
If you really think about it, a blockchain is decentralized and is more secure than traditional central databases if implemented as followed:
- Public: Anyone can join and be part of the network.
- Private: A closed network where existing nodes must vet participants before making them a part of the network.
- Hybrid: Allows a business (enterprise or startup) to have its own chain for sensitive business data and smart contract logic while achieving enterprise consensus in stages all the way to one or more public blockchains (eg BTC or ETH).
Cost
Before incorporating the blockchain, it may make sense to calculate how much it will cost. There are a couple specific areas that we’d like to bring to your attention.
Cost
Blockchain is a distributed ledger of data that is always growing. Each node in a public blockchain network maintains the blockchain by downloading the data completely and continuously to their local computer. Mainframe hardware can be leveraged. Instead of making mainframes obsolete, the blockchain is actually turning out to be the reason for banks to increase their mainframe investment.
Dragonchain's hybrid solution allows stabilize pricing with the tokenized micro-license. Usage of stable pricing (Takara) gives enterprise customers other options in addition to the advantage of having a set monthly price that can be budgeted and planned.
Power Cost
Public blockchains, especially the ones that are using proof of work for consensus, have a tendency to take up a lot of power. According to Bitcoin Luxembourg, the cost per transaction of Bitcoin since the beginning of 2018 is somewhere between $75 and $160. A major chunk of that is due to electrical costs.
So, can a public blockchain ever be truly cost-effective? Yes, but in its current state, not so much. The fact is that the majority of these public blockchain initiatives are in a proof of concept phase and it is far too early to tell if they can be effective or not.
Operations
One area where blockchain usage can be extremely helpful is business operations. Departments like auditing and quality assurance will benefit from this technology.
Auditing
Remember, blockchain is both transparent and immutable which helps in creating a permanent record of transactions. It is very simple to follow a paper trail in the blockchain for internal (and governmental) auditing purposes because the accuracy of the data is guaranteed.
Quality Assurance
Another place where blockchain can help with the business operation is in the quality assurance of the product. Since the blockchain is transparent, each and every part of the chain can be closely scrutinized and investigated.
An interesting place this is being used is in the food supply industry. Events like a salmonella contamination could be traced back to the source in seconds, and every single bag from that batch would be flagged for removal whether it be freshly packed in the processing plant, in a truck being delivered, or in the retail store already. This system could notify everyone involved in seconds rather than days.
To make this work, there is one thing a business must consider: the training of your employees.
Think about it, can you make sure that your business operations will go off without a hitch if your employees are completely clueless?
What training is available for all humans involved? Managers, software developers, customers, and clients.
Human involvement
- Managers. Managers and executives of the various division in your company need to learn about how blockchain works. They will be responsible for learning the basics of the technology and gaining an understanding of how it is going to change the processes.
- Software Developers. Developers need to understand how blockchain works and how they can develop on it. A solid understanding of what smart contracts are and how the automation works. Most blockchains have some type of conditional logic scripting capabilities. Many times, this requires the developer to learn a new language such as Solidity on the Ethereum public blockchain.
- Customers and Clients. A major concern that most businesses have is that the blockchain will disrupt their relationship with clients and customers. Humans are not very open to change unless it makes the process easier or removes friction. It's important to keep existing clients using a familiar style of operations. Compatibility with customers' systems is very important. Any blockchain enhancements should and must support existing customers.
What should you do?
Blockchain is a revolutionary technology and will disrupt businesses over a wide range of industries. However, it doesn't mean that you need to move your entire business practice over to a blockchain solution.
Explore potential use cases for blockchain technology and start building blockchain applications.
- Identity systems, including privacy, security, and confidentiality factors
- Ticketing
- Rights expression and licensing
- Digital media entitlements
- User-focused digital rights management
- Decentralized processing, computing, and storage infrastructure
- Voting systems
- E-discovery capable record keeping systems
- Legal - smart contract to encode legal agreements between parties
- Audit - reporting and compliance
- Funding, accountancy infrastructure, and tracking
- Generic crypto-store (blockchain powered transactional data store)
- Payments platform
- Organization internal currency (chargebacks)
- Modeling of organizational micro-economies (interactions and incentivization between teams)
- Open source software project governance (See Blockchain and Cryptocurrency for Free and Open Source Project Governance)
- Entitlements tracking
- Intellectual Property (IP) marketplace
- Internal/private prediction market (corporate or organization communications improvement)
- Customer facing currencies (including loyalty programs) - medium of exchange within an ecosystem (physical or virtual/gaming)
- Reservations and booking (e.g. travel, room, table) contracts
- Internet of Things (IoT) security platform (common and secure implementation for configuration, code, and firmware delivery)
- Enterprise systems
- Shared data with restricted multi-tenancy (legal and security requirements for data storage within/out international or other legal boundaries)
- Real-time Enterprise governance (rules based enterprise-wide validation of transactions and blocks - i.e. disparate segments/business units)
- Move data to the edge (edge services and mobile subscribe to data feeds of necessary data, which is held locally to the service, reducing latency and increasing service uptime/resiliency)
- Configuration management (security, traceability, and non-repudiation of configuration changes)
- Enterprise analytics (based upon all activity)
- Pay-for-performance systems via smart contracts
- Peer-to-peer financial derivatives
- Futures
- Credit and interest rate swaps
- Bonds
- Options
- Supply chain
Dragonchain's Mission
Dragonchain is the global leader in blockchain technology applications. As a blockchain service provider, we offer unprecedented flexibility, integration, and security to customers, developers, and the blockchain community.
At Dragonchain, we live by the idea that any asset can be digitized; in turn becoming the basis of a marketplace that can be created anywhere.
What is the Dragonchain Ecosystem?
The Dragonchain ecosystem is the grouping of interconnected blockchains, web tools, services, and resources built on Dragonchain.
Dragonchain provides security, scaling, and coding flexibility on a business-focused blockchain platform. The Dragonchain ecosystem serves as the toolset required to build and create blockchain business magic.
Existing platforms restrict the creation of truly secure and scalable blockchain applications for real world business use cases. Dragonchain offers:
- Protection of business data and operational smart contracts
- A scalable system via serverless deployment
- Creation of smart contracts with established, general-purpose languages (Java, Python, NodeJS, C#)
- An ecosystem for sharing and monetizing smart contracts
- Standardized processes
- Community funding via the Dragon tokenized micro-license
- A marketplace and network for blockchain-based services (i.e. token modeling)
- Access to smart contract libraries
- Dashboard visibility for markets
Dragonchain is a turnkey blockchain enterprise solution. It provides a toolkit for users to create their own blockchain solutions with greater ease and flexibility than other alternatives. With Dragonchain's currency-agnostic design, users can make their own blockchain from scratch and operate on top of existing systems. The platform can plug and play with any blockchain or software with a marketplace of people (like AWS), providing services for clients' chains and needs.
Interchain gives any businesses access to scalable, easy-to-use technology with access to all ERC20 and NEP5 tools. They are able to build their own ultimate blockchain with access to the resources of every other chain.
Our consensus mechanism serves as a "blockchain of blockchains", operating without the need of a Mainnet. Think Windows for blockchain. We are currency-agnostic, so for adoption purposes we chose an ERC20 token. We may do our own token in the future, but this would require existing technologies to also adopt a currency-agnostic model.
What is a mainnet?
It's instinctive to try to describe Dragonchain with "Mainnet" lingo— after all, the Mainnet is where the actual transactions take place right? Unlike other blockchain service providers, we interchain with other networks to transact and our clients build their own consensus, setting up their own nodes.
Why Dragonchain?
To best serve its users, a blockchain solution must be secure, scalable, and have the versatility to handle wide range of use cases. Dragonchain offers:
- Security - Enterprise-ready architecture that creates a spectrum of trust
- Development - Established language support for smart contract development (Java, Python, Node, C#)
- Scalability - Serverless deployment on Amazon AWS
- Protection of business data and processes
- Ease of integration
- Create oracles for your own blockchain
- No base currency + currency agnosticism + multi-currency support
- Interchain - Interoperability with other blockchains
- Short, fixed-length block time
Discover our blockchain platform features, the Blockchain as a Service model or take more free blockchain courses on our Academy.