Quantum Safe Blockchain In a Digital Fortress
By now, much of the nation has heard of the SolarWinds attack this past December. But, many are unaware of the severity of the situation. Individuals hacked the SolarWinds platform called Orion. According to SEC documents, approximately 33,000 SolarWinds customers use Orion to manage their IT resources. By hiding malicious code in the body of legitimate software updates, hackers had access to 18,000 of SolarWinds’ customers, many of which were high profile clients, including Fortune 500 companies and multiple agencies in the US government. Once hackers had breached Orion, they had access to everything that touched Orion.
Several high profile hacks this past year have marked a shift in the desire to finally address the vulnerabilities of our systems. Governments and businesses around the world had always thought their security systems were good enough but they are quickly realizing dated technology is not going to cut it anymore. The question is, will government agencies and industry leaders be proactive enough to do what needs to be done to keep everything secure? And if they do, will it work?
According to encryption specialist Dr. Al Carlson if we keep with the present technology, then the answer is no, not if they use the same data security that has repeatedly failed. “The technology that we have built can stop the attacks that are going on now. Whether or not leaders implement that technology depends solely on them.”
That technology includes a suite of tools that, when used together, become the best defense we have today of true data security. Let’s take a look at some of those tools, where they can be applied, and what it will take for implementation.
Polymorphic Technologies
Polymorphic Random Number Generator
The polymorphic random number generator is used to eliminate patterns in long strings of numbers. Anytime patterns emerge, those patterns can quickly be exploited. The polymorphic random number generator never cycles so you can’t find patterns. This type of encryption can secure any data set across any industry and even guard against quantum computing.
Dr. Al describes it best, “Think of doing a handshake between the computers. That gives you the initial number. The initial number selects a random number generator; a seed. Then we map that onto a physically unclonable function that’s agreed upon between the two nodes, usually by taking some information from both nodes and combining them in a known way. What that does is it points to an area in the physically unclonable function, and you read part of that. That information is then used as a seed along with the information you input and selects the next seed. So you’re running from seed to seed to seed. Before there’s enough time for an attacker to figure out what the sequence is, all those seeds replace the random number generator and you replace the physically unclonable function tables. So you end up having an evolving set of random information that you’re picking from that was determined from the original physically unclonable functions in the handshake.”
Data Camouflage
Damaging a file is a simple encryption technique to hide a pattern of a transmission inside a transmission. Data Camouflage takes a copy of a file and damages it by randomly flipping bits of information. When and where the bits flip is completely random. Some bits will flip and some won’t. What you are left with is a damaged file intertwined with an intact file and the inability to distinguish the two.
Polymorphic Random Number Generator in a Quantum Environment
There are a few problems in a quantum computing environment. Quantum computers operate much faster than classical computers. However, you still have to run them with classical computers. Modern cryptography and computing use trapdoor functions. Trapdoor functions are functions that are easy to compute forward if you have all the information, but they’re very difficult to figure out backward.
Shor’s algorithm shows that those trapdoor functions are very easily solved in the quantum environment. Trapdoor functions then become unusable as they easily compromise security and are hackable.
Also, technology is moving us away from the two key solutions with asymmetric algorithms for public key infrastructure and encryption to symmetric algorithms. But, according to Grover’s algorithm, to use symmetric algorithms the keyspace is going to have to double.
Polymorphic encryption multiplies the effect of keyspace through compression, making it many times bigger for very little incremental effort. This means that you can use symmetric algorithms for key structure and encryption.
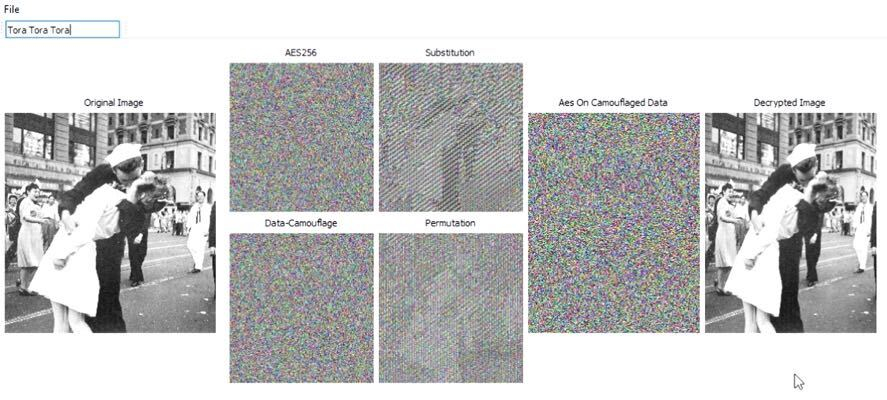
Simply adding these polymorphic technologies makes data quantum-safe. Take this data camouflage demo as an example.
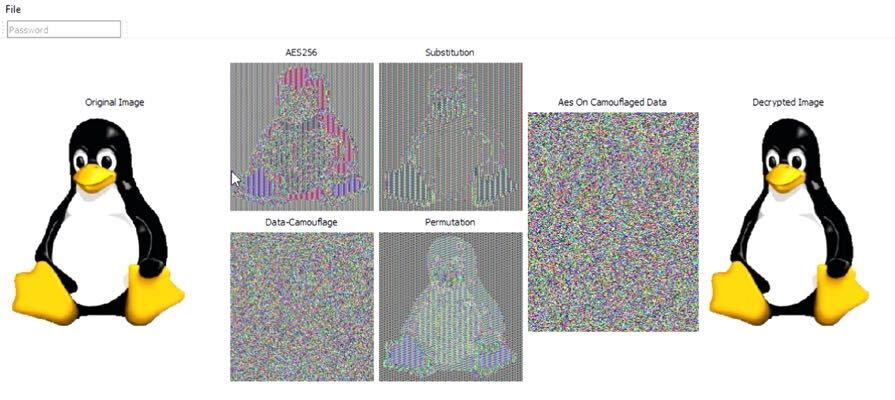
Here is an encrypted file. We can enter a password to open the file.
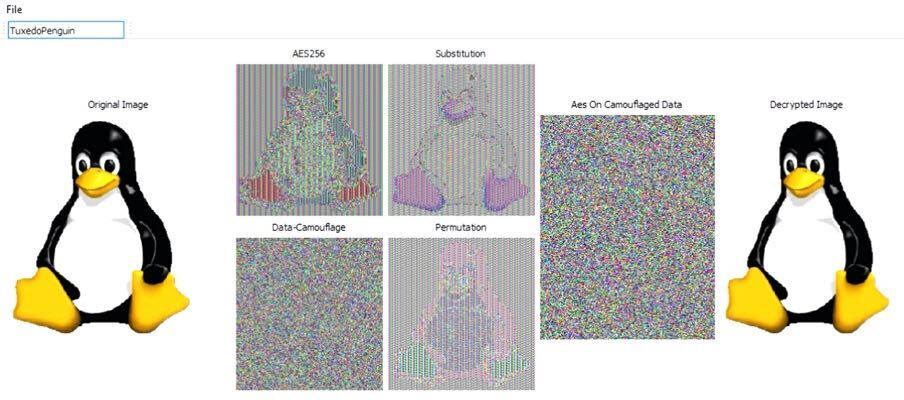
Here you see vertical striping or patterns. The bottom left image shows the data camouflage. No patterns are visible due to the flipping of bits.
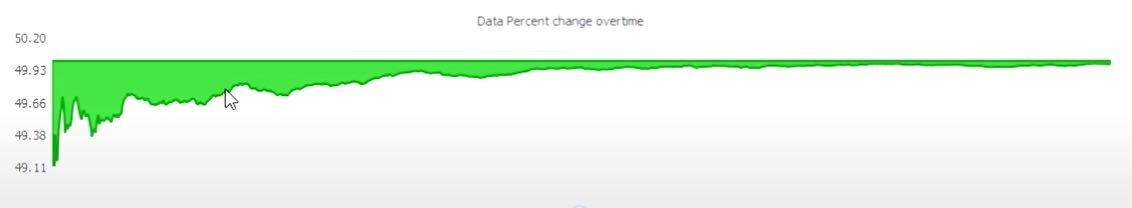
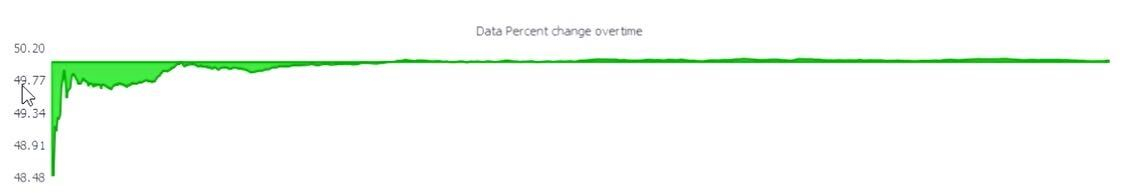
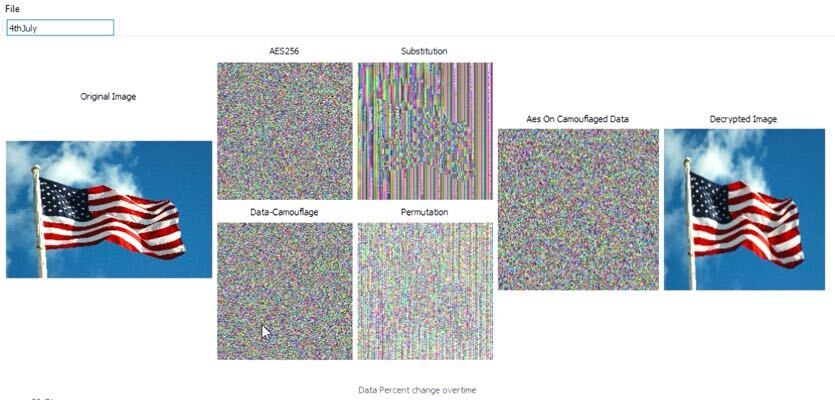
This graph shows what percentage of bits have been changed. The longer you look at that and the amount of data, you can see that it settles down at around 50 percent.
This image shows the same file but the rate of flipping and the specific bits that flipped is different than the first one. Every time this file is encrypted the data camouflage is different.
Notice how the change over time is different each time you view the file.
Here is a large back and white photo file. AES256 does a decent job but if you look closely you can still make out a silhouette of the running from top right to bottom left.
This is the same with the American flag. The AES256 still shows a shadow of the flagpole.
When inserting damaged files into pixels containing intact files a quantum computer gets distracted trying to figure out why this file is damaged. The quantum computer gets bogged down and doesn’t know what to do. It’s not uniform but that is the point. All those patterns that would otherwise be like candy for a quantum computer are non-existent. It’s deterministic randomness.
Where Blockchain and Polymorphic Random Number Generators Collide
Blockchain has natural fragmentation of the data in each block. The fragments are small and perfect for a shard. When polymorphic encryption is applied to blocks, the result is much better encryption, quickly, without bogging down systems.
For instance, you can damage an encrypted file and then put a copy of that damaged encrypted file into any block. To access the information within the block you would have to know many sequential polymorphic random numbers to reconstruct the seed to remove the damaged files, reveal the initial information and recover the data.
If somebody gets really lucky and breaks one block, they only get a little bit of information. The rest of the blocks have different encryptions and are unrelated. The polymorphic number generator adds another layer of security to businesses already using blockchain.
Digital Fortress for Interoperability and Cybersecurity
Supply chains, Health Care, and Energy are some of our most targeted infrastructures for hackers. General Motors once told new Dragonchain partner and CloudFace founder, Phil Abraham, that there are a million different places hackers could easily access a supply chain, but suppliers and vendors aren’t being proactive to secure those areas. This leaves the supply chain-wide open for attacks. That has all changed. According to Phil, call after call ends in cybersecurity. For the first time, Digital Fortress combines interoperability between systems and quantum-safe cybersecurity.
CloudFace
CloudFace has been helping global companies reduce risk and maximize their bottom-line impact by using a combination of artificial and human intelligence, incorporating "complexity science" and proprietary algorithms that are quantum-proof and secure. CloudFace along with long-time business associates, AQED, and Dr. Al Carlson is working to secure supply chains in every sector.
AQED
AQED takes polymorphic technologies and turns them into a program that would make it easy for the average individual to use to secure any system now and into the future. AQED knows you don't have to spend a billion dollars to be quantum-safe. You just have to do it differently.
Dragonchain
Dragonchain’s patented interoperability system, Interchain, removes the complexity involved when connecting any of the organization’s systems, whether it is their supply chain, accounting, or IT systems.
Achieving interoperability and secure CCPA/HIPAA/GDPR capable data portability has been a problem for organizations even without a blockchain element. So much so that many have shied away from blockchain technology. But, by using Interchain to connect disparate systems that otherwise would still struggle with connectivity, organizations can finally overcome the barriers to interoperability.
The architecturally focused hybrid system allows a business to maintain full control of its data with a private blockchain. The proof of an event is then decentralized across multiple public chains for transparency, accountability, and security. When you need to prove a data set, then you can expose it. When exposing the data, anybody can see how the proof was secured up the chain to Bitcoin and Ethereum for confirmation. The proof then contains about ten billion dollars worth of immutable security behind it within a few years.
Interoperable systems connected with quantum-safe blockchains secured by polymorphic technologies can be applied to any sector including Government agencies, Insurance, Banking, Energy, Automotive, Real Estate, Information Technology, Health Care, or any supply chain; anywhere there is data.
“The goal is to bring interoperability through blockchain and secure data with quantum-safe encryption. Digital Fortress is basically an easy button for governments, businesses, and vendors to shore up their existing IT systems, ” - Phil Abraham
Going Forward
As technology continues to seep into every aspect of our lives, companies must build on a strong secure foundation. Data must remain secure whether it is at rest or in motion. Everything must be encrypted at all times. By everything we mean everything. IoT, MIoT, and IIoT devices. These devices need to be built on top of security not apply security after the fact.
The foundation of cybersecurity is broken. Built too long ago on the assumption that there would never be enough computing power to break modern algorithms. We now know that to be misguided. Forward-looking governments, SysOps, and DevOps administrators for businesses are well served by the flexibility, time to market, and scalability of the first quantum-safe blockchain. By using a Digital Fortress systems are protected today and well into the future.
Learn how Dragonchain segregates data from proof or contact us. Dragonchain provides a quantum safe blockchain environment inside a digital fortress.